
Leaked Geofencing Keys — Remote ID and EW Notes
Consumer drones and tactical UAVs now share supply chains, radios, and software habits. As a result, a “small” security lapse can scale into a real defense problem. This post links three themes that keep resurfacing: leaked geofencing keys, Remote ID “bypass” chatter, and EW field notes—without offering a how-to for wrongdoing.
What “key leaks” usually mean
When communities mention a manufacturer “leaking keys,” they often mean cryptographic material escaped into public view: TLS private keys, firmware-signing keys, or cloud credentials that protect update services. In 2017, reporting alleged DJI left private keys and other sensitive items exposed via GitHub and related infrastructure, showing how developer hygiene can become a product-security issue.
A different route is insider error; back in 2019, multiple outlets reported a former DJI employee uploaded code to GitHub and received a prison sentence and fine in China. Neither incident proves an attacker can instantly “own” a fleet. However, both weaken the trust model behind updates and services.
Geofencing Shifts to Geo-Awareness
Many people still picture geofencing as a formidable barrier. Vendors have been moving towards advisory models that place responsibility back on the pilot. DJI’s GEO update for the United States (January 2025) replaced prior datasets with FAA data and, in some locations, changed restricted zones into enhanced warning zones. Aviation reporting also noted DJI removing electronic restrictions that previously prevented flight near airports and other sensitive sites. Therefore, the security focus shifts. The main question becomes: can you trust the software and data that shape geo-awareness, rather than assuming a “fence” will always stop behavior?
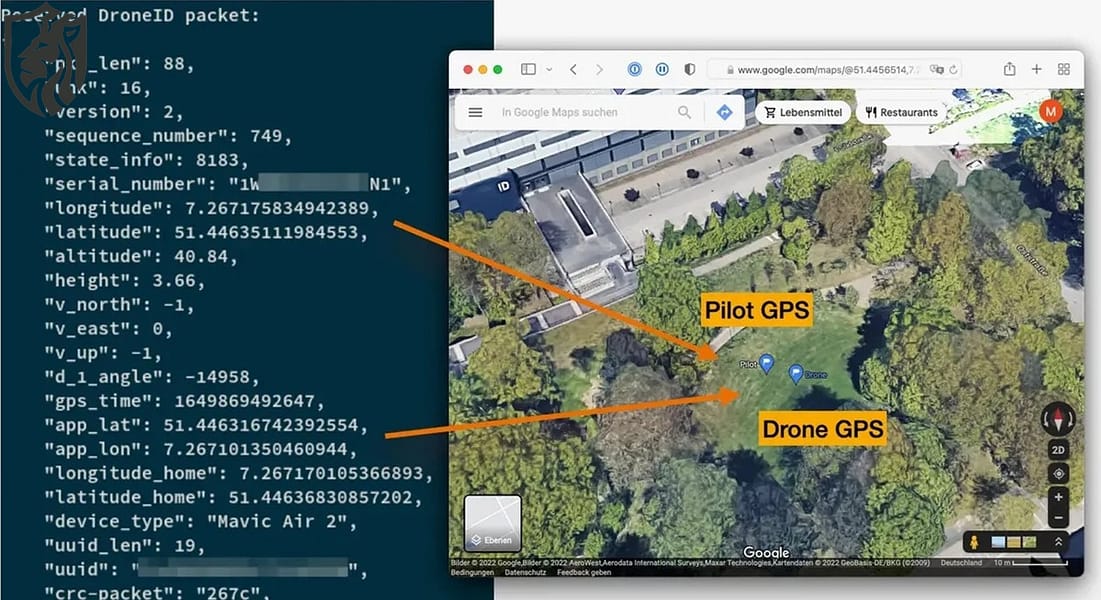
Remote ID Aids Detection, Trust Still Debated
Remote ID aims to make drones visible in flight. In the United States, 14 CFR Part 89 establishes basic rules for how drones should perform, such as sending out at least one message every second and being accurate about their location (for instance, within 100 feet most of the time), while also needing to be secure against tampering. Yet broadcast identity is only useful if receivers can trust it. The IETF’s Drone Remote Identification Protocol (DRIP) focuses on using cryptography to prevent fake signals, and related documents talk about issues with replay and authentication in current methods. That is why defenders should treat Remote ID as one sensor input, not an oracle.
October 2025 Leak: Shows UAS Trust Breaking
In October 2025, researchers reported a leaked Russian FPV drone field manual (dated 2024) circulating online. It catalogued common quadcopter builds, payload options, and frontline EW/ECM practices—effectively turning hard-won “field notes” into open source. At the same time, a 2025 CISA detection-technology brief warned that Remote ID signals can be spoofed or tampered with, letting adversaries broadcast false drone data. Add any weakness in vendor geofencing or update trust, and defenders face attribution fog, deconfliction mistakes, and wasted counter-UAS cueing—pushing commanders into slower, riskier decisions. Even without a working exploit, leak-and-spoofing trends let attackers mislead sensors and delay response today.
How to Judge “Bypass” Claims
Online claims often mix three things: (1) legal unlocking workflows, (2) misconfigured receivers, and (3) genuine security flaws. Therefore, analysts should ask simple questions. Does the claim reproduce across firmware versions? Does it depend on cloud access, or does it persist offline? will a vendor rotate credentials, change signing material, or ship a patch? Finally, can independent researchers validate the behavior without publishing exploit steps? These checks keep assessments grounded while still treating the risk seriously.
EW Field Notes: Spectrum Wins
In a contested environment, EW dominates outcomes. A U.S. Army professional journal article describes FPV drones as low-cost (about $500), carrying roughly 0.7–3 kg warheads, flying up to around 120 km/h, and typically operating over 5–10 km. It also notes FPV drones took a leading role—“up to 70 percent”—in causing losses to equipment and manpower. RUSI reports dense Russian EW coverage (at least one major system per 10 km of front) and Ukrainian UAV losses around 10,000 per month.
RAND references estimates in the same range, reinforcing how quickly drones became consumables under jamming pressure. IEEE Spectrum describes the rapid iteration loop this creates and the push towards autonomy and GNSS-denied navigation when links fail. These realities explain why identity, updates, and navigation resilience now matter as much as airframe performance.
Why It’s a Serious Military Risk
Leaked geofencing keys and Remote ID “workarounds” can undermine confidence in the entire drone control chain. When forces cannot trust firmware, geo-awareness alerts, or broadcast identity, they lose speed in airspace management and struggle to attribute incursions. Moreover, an adversary can inject misleading tracks, blend hostile drones into civilian patterns, or overload operators with noise. Meanwhile, EW field experience shows jamming and spoofing already drive high loss rates and frequent mission failures. The threat is thus primarily operational: weaker deterrence, increased fratricide risk, and slower decision-making. Instead of acting quickly, commanders must verify what is real, while seconds matter.
Defensive Takeaways Without a How-To
- Harden updates trust. Treat signing keys and updating credentials as mission assets. Enforce hardware-backed key storage, strict access control, and rapid revocation. Also audit developer pipelines for accidental secret exposure.
- Harden identity truth. Fuse Remote ID with RF detection, radar, EO/IR, and behavior analytics. Track standards that add cryptographic assurance (DRIP-style ideas) so you can separate “seen” from “trusted.”
- Harden EW operations. Assume link loss and GNSS degradation. Build procedures that degrade gracefully and deconflict friendly jammers. For more schorlarly defense related articles visit Defense News Today’s Cyber Security section
Future hints
Manufacturers will likely keep moving towards geo-awareness models, which increases the importance of trustworthy zone data and updates. Meanwhile, Remote ID will face pressure to become more verifiable, because spoofing at scale is a public-safety hazard. Finally, EW will keep compressing innovation cycles, pushing autonomy and jam resistance into mainstream designs. In that context, leaked geofencing keys are not just a headline. They are a reminder that drones now live in a security ecosystem, not a gadget ecosystem.
References
- https://www.ecfr.gov/current/title-14/chapter-I/subchapter-F/part-89
- https://viewpoints.dji.com/blog/geo-system-update
- https://datatracker.ietf.org/doc/rfc9434/
- https://www.rusi.org/explore-our-research/publications/special-resources/meatgrinder-russian-tactics-second-year-its-invasion-ukraine










